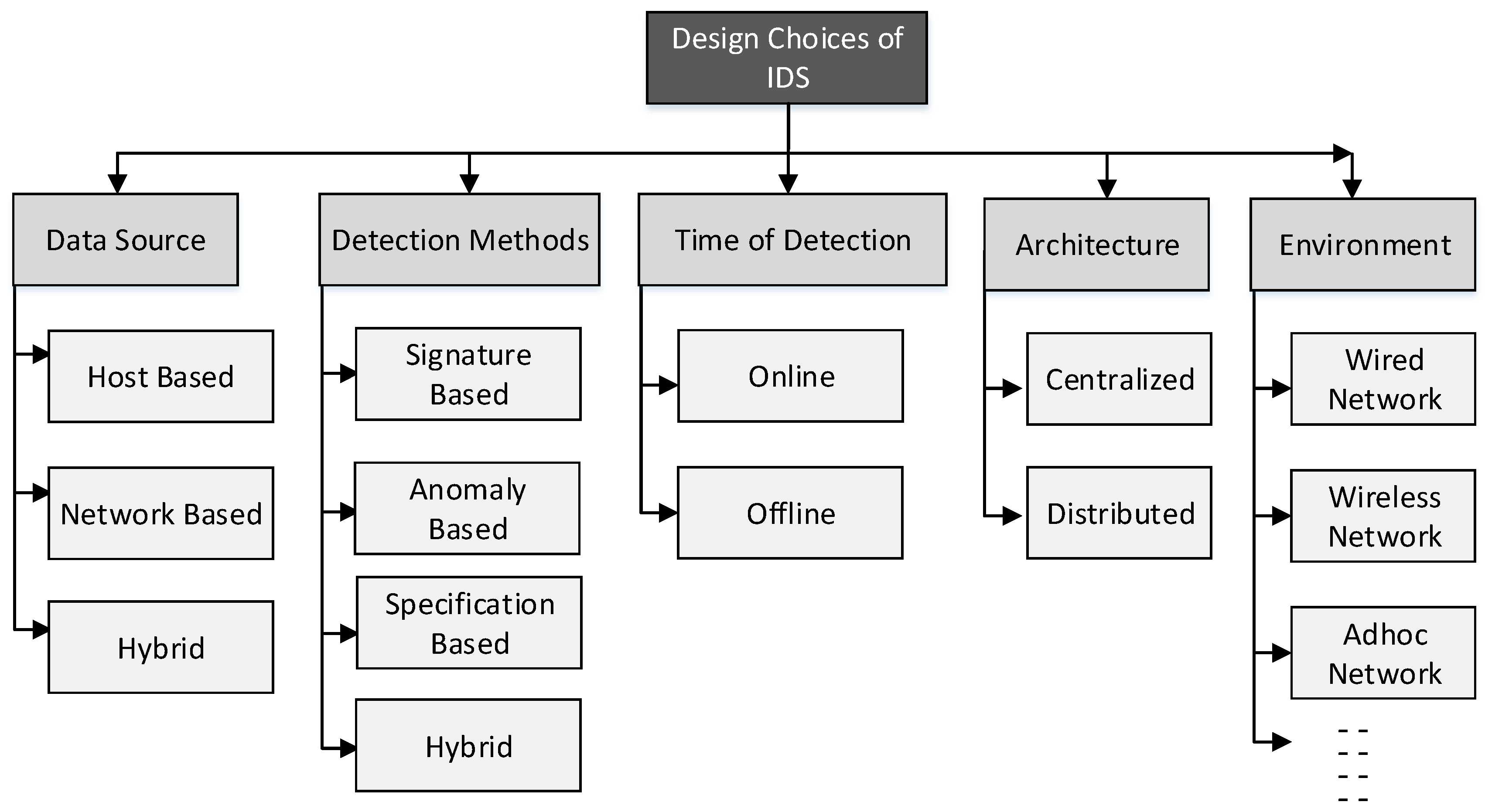
Electronics | Free Full-Text | A Review of Intrusion Detection Systems Using Machine and Deep Learning in Internet of Things: Challenges, Solutions and Future Directions | HTML
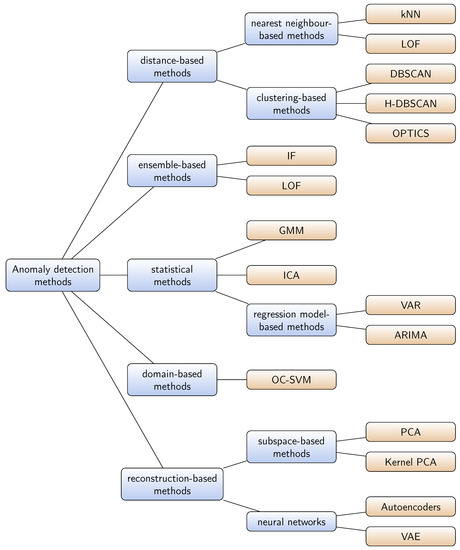
Aerospace | Free Full-Text | Recent Advances in Anomaly Detection Methods Applied to Aviation | HTML

Network intrusion detection system: A systematic study of machine learning and deep learning approaches - Ahmad - 2021 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library
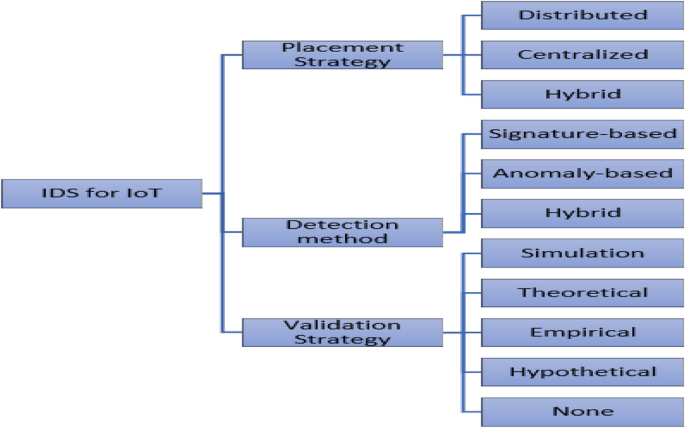
A critical review of intrusion detection systems in the internet of things: techniques, deployment strategy, validation strategy, attacks, public datasets and challenges | Cybersecurity | Full Text

Network intrusion detection system: A systematic study of machine learning and deep learning approaches - Ahmad - 2021 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library

Deep Learning for Anomaly Detection: A Comprehensive Survey | by Guansong Pang | Towards Data Science

Top 10 Anomaly Detection Software in 2022 - Reviews, Features, Pricing, Comparison - PAT RESEARCH: B2B Reviews, Buying Guides & Best Practices
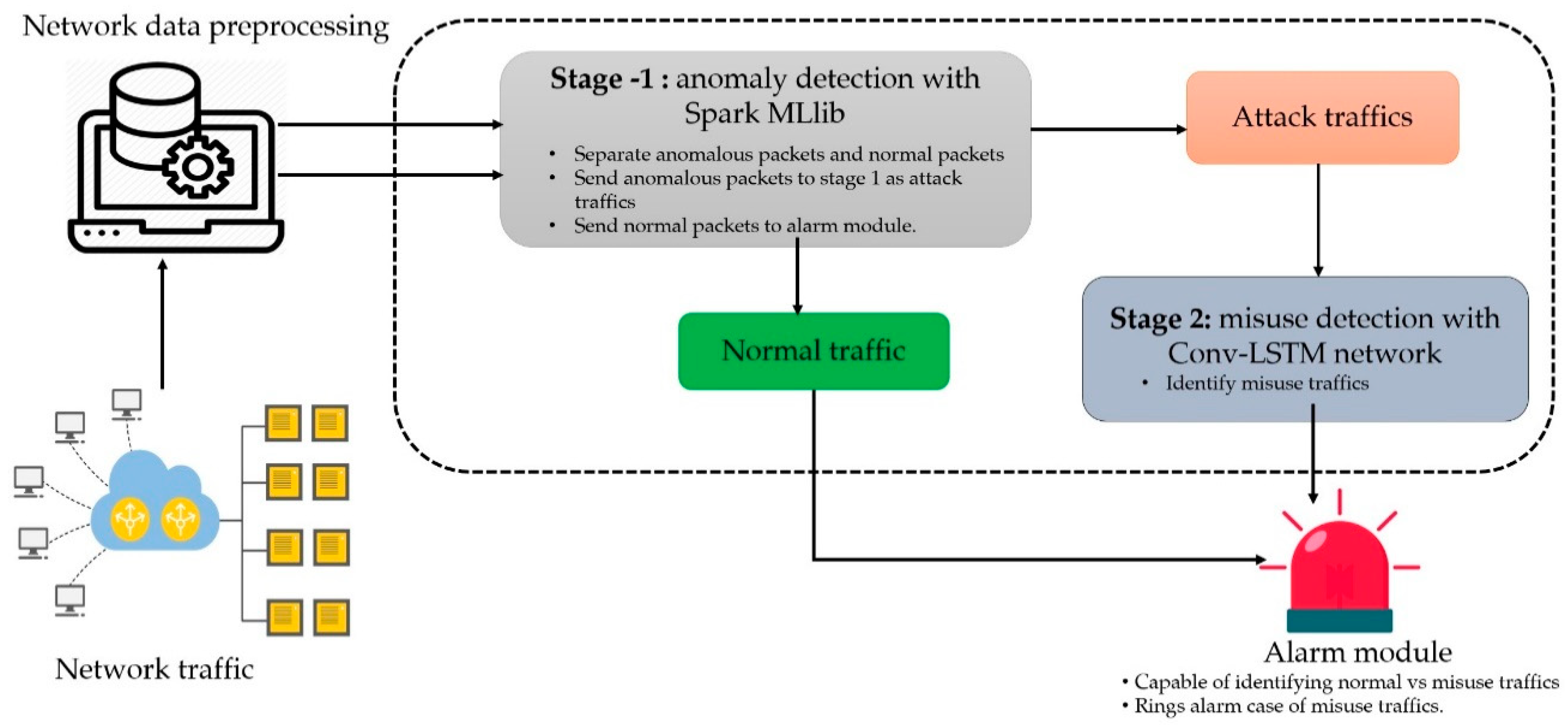
Symmetry | Free Full-Text | A Scalable and Hybrid Intrusion Detection System Based on the Convolutional-LSTM Network | HTML
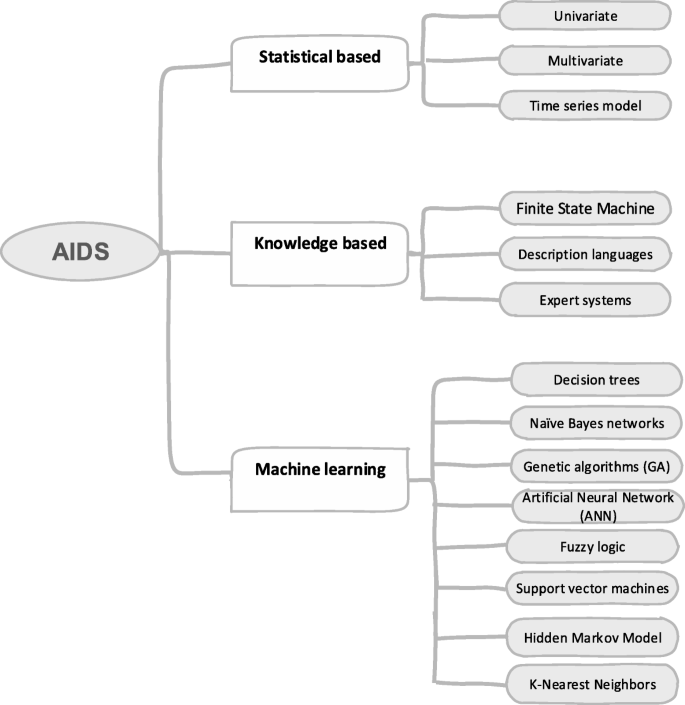



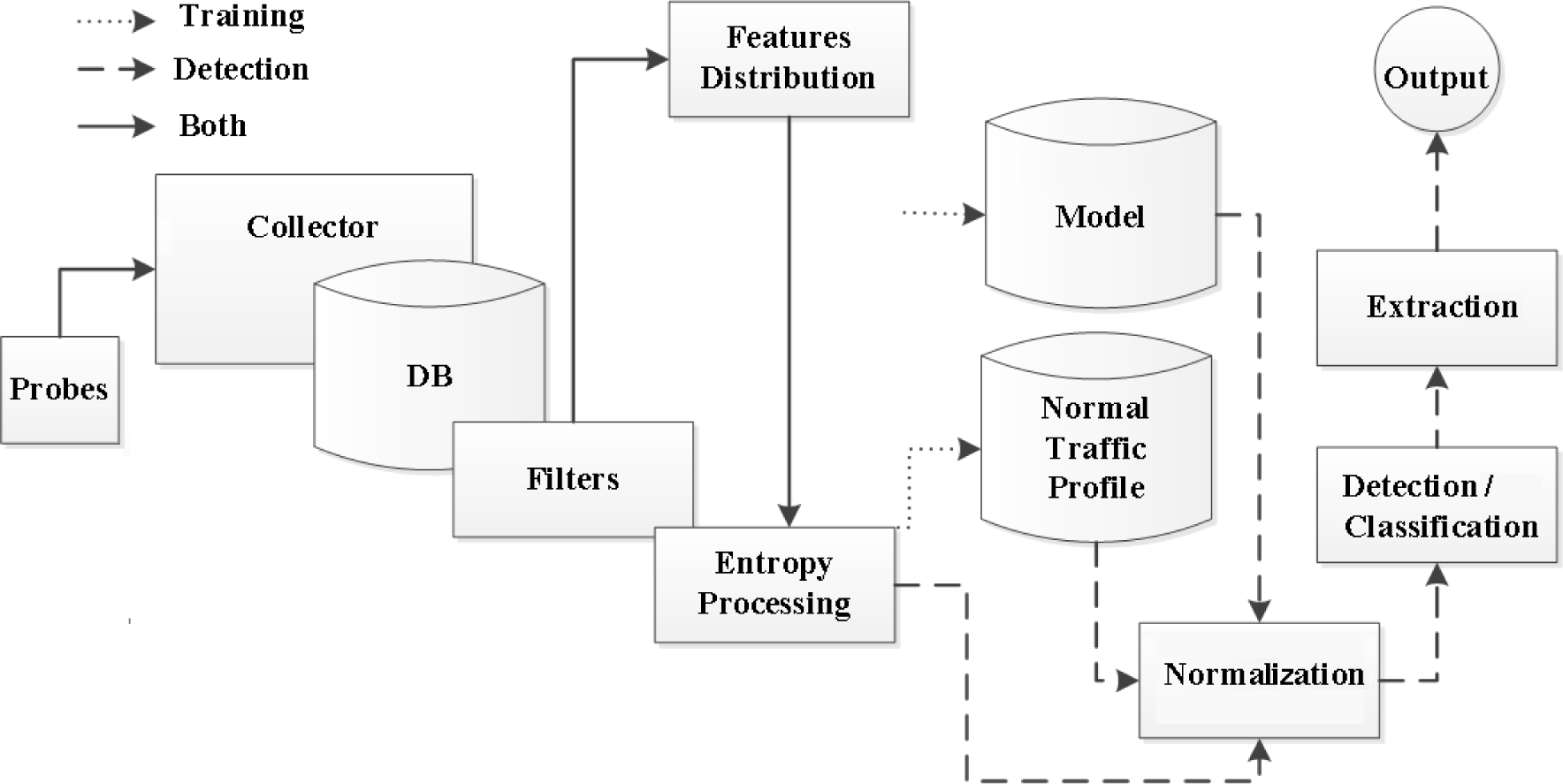
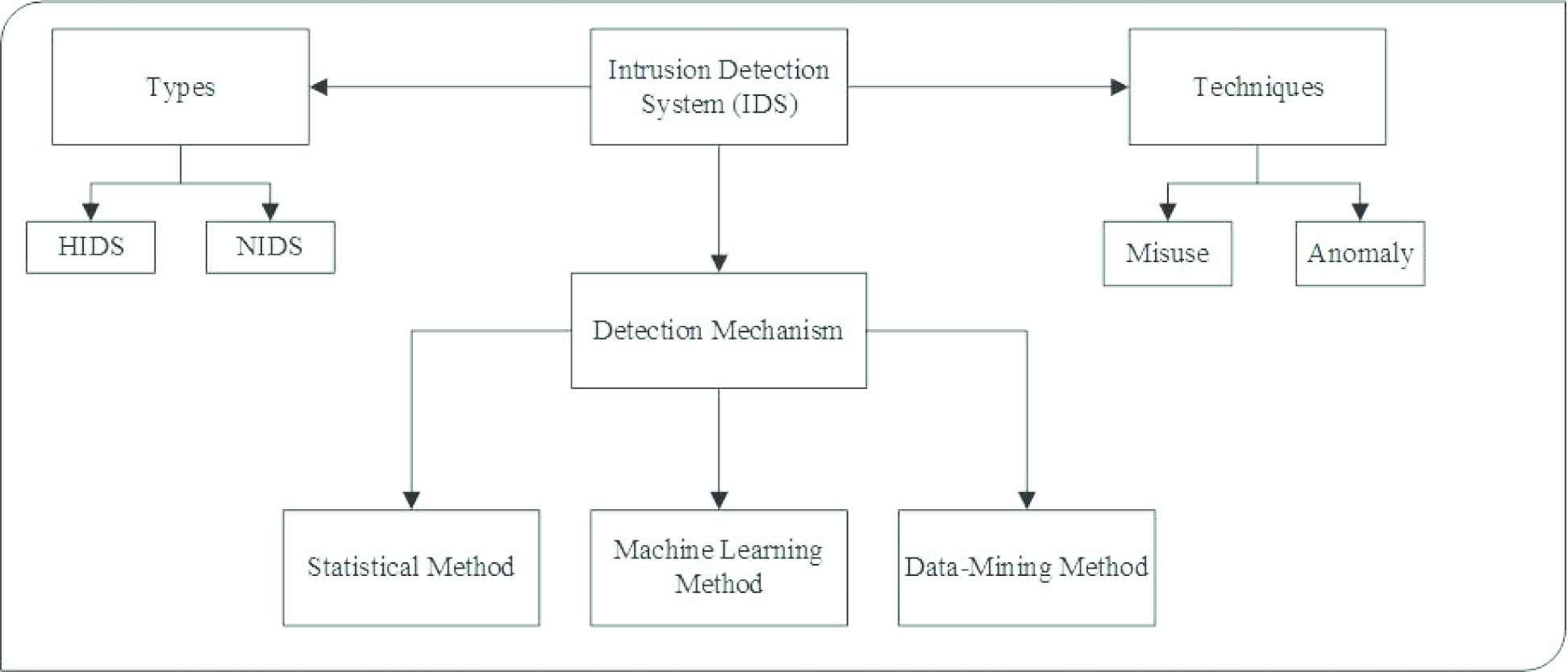
![PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e467ff1ea3a0c535a0cef87f7e0daa414d524d9d/16-Figure11-1.png)

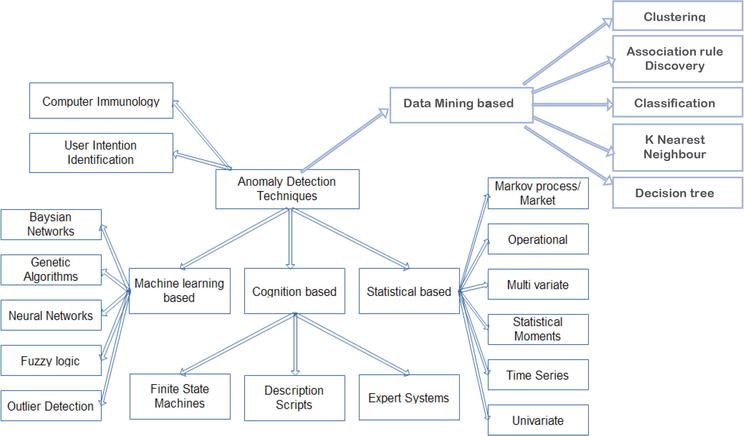
![PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e467ff1ea3a0c535a0cef87f7e0daa414d524d9d/5-Figure1-1.png)


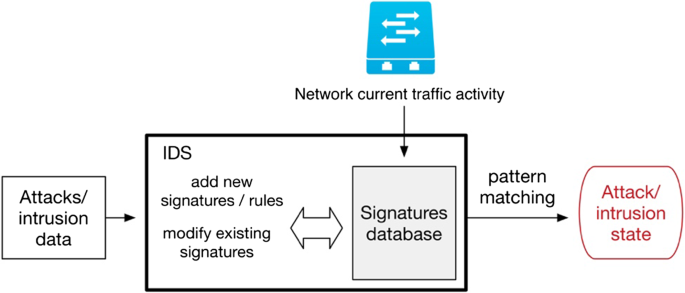
![PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e467ff1ea3a0c535a0cef87f7e0daa414d524d9d/18-Figure12-1.png)
![PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e467ff1ea3a0c535a0cef87f7e0daa414d524d9d/20-Figure13-1.png)